 Introduction
Introduction
Hotels — particularly budget properties — have long been identified as common venues for human trafficking activity. Yet efforts to intervene often fail because staff lack structured tools for recognizing trafficking indicators in real time, and existing monitoring approaches sometimes raise legitimate legal and privacy concerns.
By applying ASIS-style security risk management principles and aligning with DHS trafficking red flag frameworks, it is possible to design an automated monitoring system that both maximizes detection yield and minimizes legal blowback. The key is to focus on high-percentage, low-risk automated red flags already rooted in hotel operations, then layer them into a scoring system that escalates only when multiple anomalies converge.
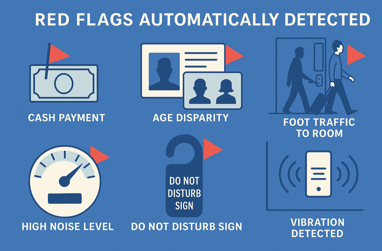
High-Percentage, Low-Legal-Risk Automated Red Flags
These indicators can be monitored automatically with very low chance of judicial or defense attorney challenges, because they rely on data already captured for property security, fraud prevention, or guest safety.
-
Payment Method Flags
- Cash payments, prepaid debit card use, repeated declined cards.
- Already standard fraud-prevention practices; easily extended to trafficking.
-
Guest Identity / Age Disparity Flags
- Adults checking in with minors not clearly related.
- Multiple IDs from unrelated young women linked to one older male.
- Included in DHS/Polaris red flag lists; defensible as business safety checks.
-
Entry / Access Control Flags
- Guests bypassing the lobby, entering directly on foot, and going straight to rooms.
- Smart lock or camera logs showing repeated high-volume entries.
- Defensible as property security monitoring.
-
Noise / Decibel Monitoring (Hallways & Common Areas)
- Hallway sensors detect repeated disturbances, fights, or excessive occupancy.
- Safe if decibel-only (not recording speech).
- Courts equate this to smoke/fire alarms — safety, not surveillance.
-
“Do Not Disturb” Overuse Flag
- Rooms under DND for multiple days, especially when paired with cash payment and visitor anomalies.
- Already monitored for housekeeping and guest welfare.
-
Vibration / Impact Sensors (Common-Area Placement)
- Detect fights, loud impacts, vandalism, or overcrowding.
- Safe when deployed in walls, stairwells, or hallways.
- Must be framed as disturbance monitoring, not intimate activity detection.
Additional Automated Red Flags to Strengthen Detection
Beyond the “core six,” several expanded indicators can be integrated with minimal additional risk:
-
High Room Turnover / Short Stays
- Multiple single-night bookings or frequent early checkouts.
- Available through PMS (Property Management System) data.
-
Multiple Room Keys / Extra Key Requests
- Requests for many duplicates → suggests unregistered occupants.
- Automatable via keycard system logs.
-
Wi-Fi Network Load Monitoring
- Detection of unusually high device counts (10–15+).
- Indicates “business operation” activity.
- Safe if measured at the network level only (no content captured).
-
Unusual Supply Requests or Refusals of Service
- Frequent requests for extra towels, sheets, or trash removal.
- Repeated refusals of housekeeping beyond DND.
- Already logged in hotel service management systems.
-
Geofencing / License Plate Recognition
- Vehicles making repeated short visits or circulating frequently.
- Defensible as external property security monitoring.
-
Excessive Door Access Attempts
- Multiple failed keycard swipes.
- High-frequency in/out activity cycles.
- Already captured by lock management systems.
-
Cross-Matching With Escort Ads
- Using web scraping (like DeliverFund’s model) to correlate escort listings with hotel addresses and booking anomalies.
- Not a physical sensor, but a powerful data integration layer.
Legal and Privacy Considerations
The legal defensibility of these red flags rests on several principles:
- Use Existing Hotel Systems: PMS, keycard, noise sensors, and service logs are already collected for security and operations. Using them for trafficking detection does not create new surveillance.
- Common Areas vs. Private Rooms: Sensors must remain in common or semi-public spaces, or at an aggregate system level (e.g., Wi-Fi device counts, not packet contents).
- Layered Thresholds: No single datapoint should be treated as proof of trafficking. Instead, weighted scores determine escalation.
- Framed as Safety, Not Surveillance: Positioning matters. These tools protect guests, staff, and property, and only secondarily serve anti-trafficking functions.
Best Practice: The Layered Red Flag System
The system works like a fraud detection engine in banking:
- Each indicator adds a score (e.g., cash payment = +2, multiple visitors = +3, unusual Wi-Fi load = +2).
- Once a threshold (e.g., 6–8 points) is crossed:
-
-
Manager Check → welfare knock/visit.
-
Security Report → internal escalation.
-
Law Enforcement Referral → only when corroborated by multiple high-weight indicators.
-
This ensures privacy is preserved while still catching patterns too complex to dismiss as coincidence. Defense attorneys cannot argue “innocent explanation” when five or six anomalies converge.
Priority Ranking of Core Indicators
Based on legal defensibility and yield, the top indicators are:
-
Payment method monitoring (cash, prepaid, unusual declines)
-
Guest ID / age checks at booking/check-in
-
Smart lock entry/exit logging (visitor volume)
-
Hallway decibel-only noise sensors
-
Do Not Disturb (multi-day concealment)
-
High room turnover / short stays
-
Duplicate or multiple key requests
-
High device count on Wi-Fi networks
-
Suspicious vehicle visits (license plate logs)
-
Cross-matching with online escort listings
Conclusion
By combining operationally normal hotel data with ASIS-style layered red flag analysis, hotels can build an automated anti-trafficking system that is:
- High-percentage in detection yield.
- Low-risk legally and ethically.
- Defensible in court because no single datapoint is treated as incriminating.
- Aligned with existing business practices in fraud prevention and guest safety.
The outcome is a system that balances advocacy goals, industry standards, and constitutional privacy protections, making it both effective and sustainable.
Master Resource List on Trafficking Red Flags & Security Frameworks
DHS Blue Campaign (U.S. Department of Homeland Security)
- Risk Management and Prevention in the Hospitality Industry (Hotel Management)
https://www.hotelmanagement.net/operate/risk-management-and-prevention-human-trafficking
Industry article discussing how hotels can implement risk management practices and integrate DHS Blue Campaign principles into daily operations.
ASIS International
- Enterprise Security Risk Management (ESRM) Presentation – ASIS Chicago Chapter
https://asischicago.net/images/ASIS_International_ESRM_Slideshow.pdf
Explains ESRM, integrating security risks like trafficking into organizational risk management — the backbone of a layered red flag system. - No Vacancy for Human Trafficking
- Human Trafficking in Casinos: The Ghost Crime Operating in Plain Sight
✅ Summary
- DHS = Practical toolkits for hospitality staff (frontline red flags).
- ASIS = Risk assessment standards, ESRM models, and professional training (security framework + credibility).
Together, these three sources form a solid foundation for your essay, blog, or advocacy plan — they give you the “why,” the “what,” and the “how.”
